Single sign-on with OpenID Connect
The SSO feature is enabled on Advanced and Ultimate plans, and is otherwise available as an add-on.
Huwise allows access to your workspace to be managed through a single sign-on (SSO) authentication solution, and currently supports the OpenID Connect and SAML 2.0 protocols.
For information on how to map your SSO groups to your Huwise groups, see here.
Setting up an OIDC provider
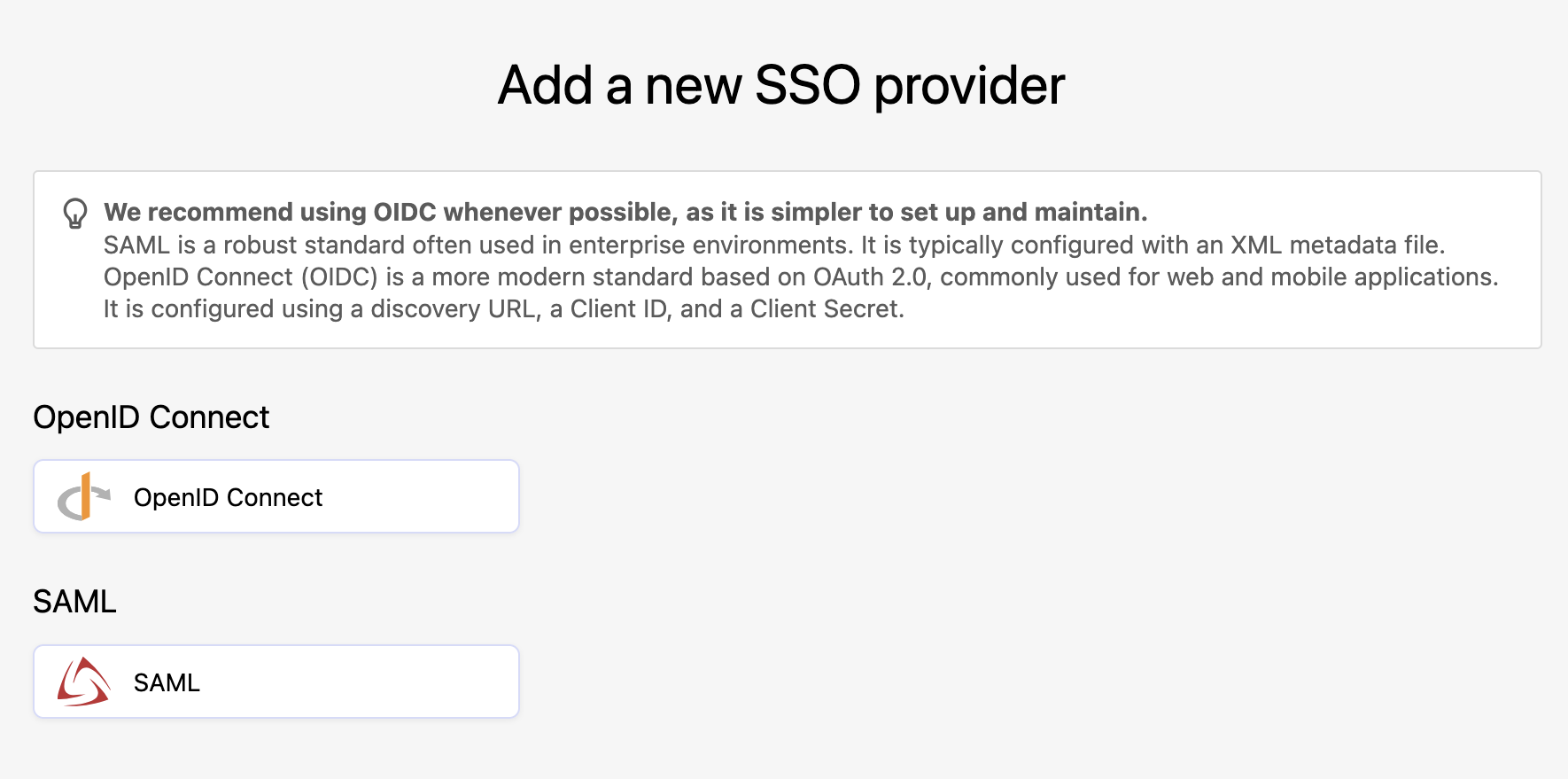
In the back office, under Access > SSO, click on Add a provider in the upper right-hand corner, then click on the OpenID Connect button.
Make sure your provider's page is open during this configuration, as you'll need to both retrieve information from it and add information to it.
You have five steps to complete, clicking Next as you complete each step:
Step 1: Provider type
Select OpenID Connect.
Step 2: Name
Enter in the name you wish to use for this provider configuration. This is the name you'll see in your list of providers.
Step 3: Credentials
You need to copy the information from here — redirect URI, back-channel logout URI, and post-logout URI — and past it into your identity provider's configuration interface.
When creating the identity provider, the redirect URI you configure is also the URL that end users will use to log in. Make sure this URL is correctly defined and communicated to users who will authenticate through this provider.
Step 4: Identity
Your identity provider will provide either a URL or a file to allow you to connect to it. We recommend using the URL whenever possible, as it is easier to manage and keep up to date.
Step 5: Service
Enter the client ID and client secret provided by your identity provider. Make sure these values match exactly what is configured on the provider side, as incorrect credentials will prevent authentication.
Authentication Context Class Reference (ACR) values are optional and only required for advanced authentication configurations.
Once you click Create provider in step 5, your new configuration appears in the list.
You are then redirected to the identity provider edit page, where you can finalize the configuration by accessing additional settings, configuring group mappings if needed, and activating the provider.
Editing an OIDC configuration
When editing a configuration, you have access to a Configuration tab and a Group mapping tab.
Configuration tab
The Configuration tab gives you access to all of the information provided when the configuration was first set up, such as the name you gave the configuration and information you used to configure your identity provider, or the URL or file you used from your IdP for the configuration.
Other settings of note:
Advanced settings — Note that under "Advanced settings," you will find options to manage your configuration's scope and attributes, such as the first name, last name, and email claims. These default to OIDC standard attributes but can be specified differently if necessary.
Additional scopes: Scopes in OpenID Connect are used to define the set of information (claims) an application would like to receive about a connected user. By default, Huwise uses the following scopes: openid, profile, and email. These scopes make it possible to authenticate a user and to retrieve their email, first name, and last name.
You can use additional scopes to add claims as additional attributes in a user's profile and use them in a dataset's security filters.Additional claims: Claims are attributes that are collected during the authentication process and that describe the user. Additional claims are required for group mapping and conditional access if claims are not already present by default.
By default, Huwise only stores claims received through additional scopes. You can store additional claims in the user profile. These claims can then be used in a dataset's security filters.
Note that these scopes and claims are what you can use to map your directory to groups in Huwise.
Authentication Context Class Reference (ACR) values: Optional and allow you to request a specific authentication level from the identity provider (for example, multi-factor authentication).
Leave this field empty unless your identity provider requires specific ACR values.
Security & behavior — Under "Security & behavior," you have four toggles, all turned off by default:
Disable local user provisioning: If enabled, users who sign in via OIDC will not have an account automatically created on the portal if one doesn't already exist.
Accept login for users whose email has not been verified: By default, only users with an email_verified claim set to true in their ID token will be allowed to log in.
Upon logout, also logout from OpenID provider: Also known as Single Log-Out (SLO). When enabled, when a user logs out of this portal they will also be logged out from the identity provider. This requires a valid end_session_endpoint from your provider's configuration.
Enable direct authentication with JWT bearer tokens: When enabled, non-interactive (machine-to-machine) authentication is allowed using a signed JWT, typically for API calls. This is an advanced use case.
Conditional access — Conditional access allows you to restrict access to users based on specific claims returned by the identity provider in the ID token. When configured, only users whose authentication token contains the expected claim (and value, if specified) will be authorized to access the application.
If no claim is selected, no restriction is applied and all authenticated users are allowed.
You can optionally define a claim value to enforce a stricter condition.
If the claim value is left empty, the system will only verify that the claim is present in the token, regardless of its value.
This condition does not apply to direct authentication using JWT bearer tokens.
Log in & profile — Under "Log in & profile," if a URL is provided, users who log in via OpenID Connect will see a link on their profile page to manage their account directly at the identity provider. Language-specific labels can be provided for this link for your portal's languages.
Group mapping tab
For information on how to map your SSO groups to your Huwise groups, see here.